Custom Model Development
Models are Excel-based and can use basic or advanced probabilistic methods.
Custom Cyber Risk Models: From Qualitative to Quantitative Custom-developed cyber risk models can be tailored to any organization’s needs, ranging from simple frameworks that convert qualitative risk ratings into quantitative values, to sophisticated mathematical approaches.
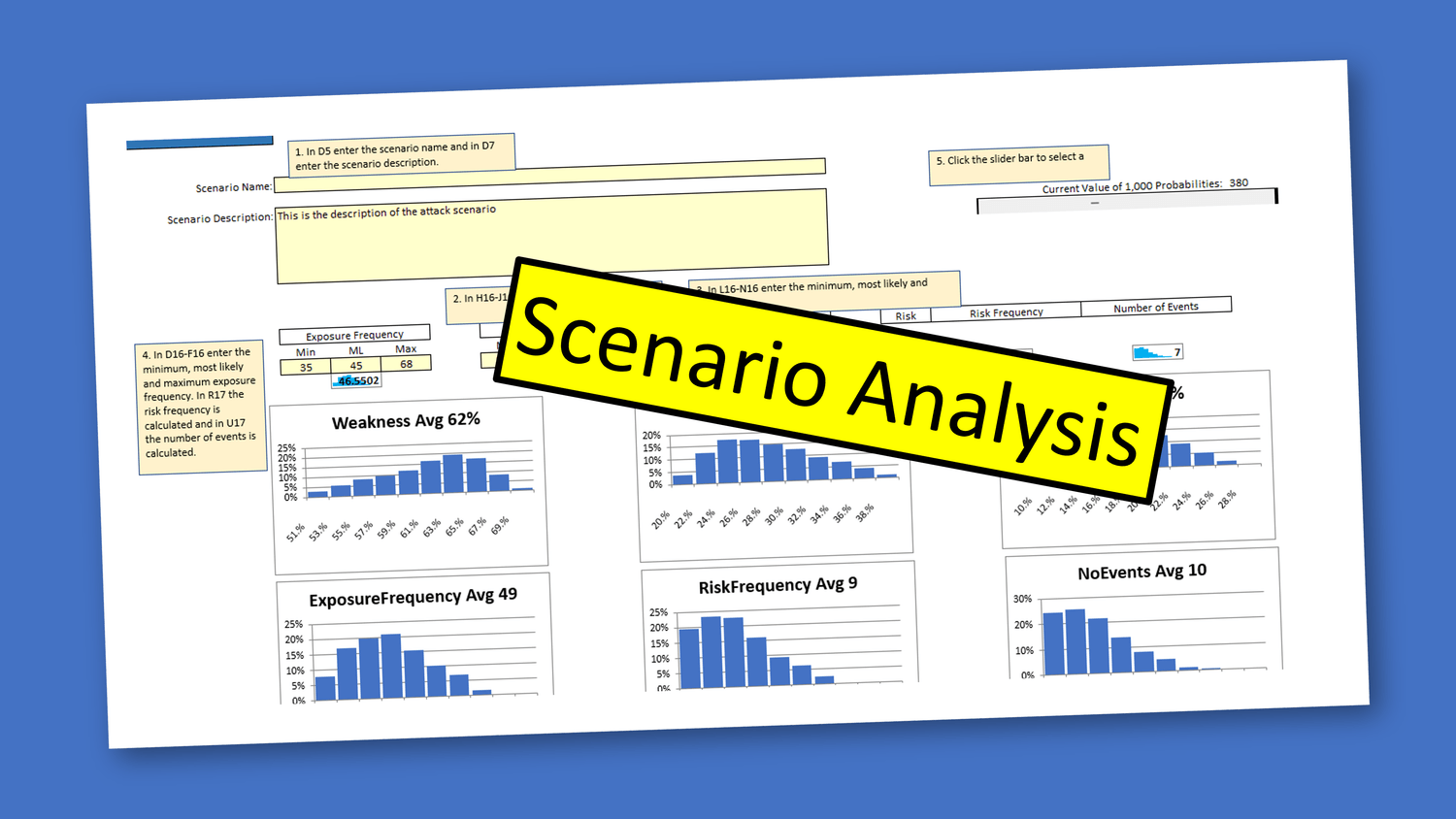
Scenario-Based Modeling: The Foundation of Effective Risk Estimation Scenario-based modeling is a foundational technique for estimating cyber risk. By developing realistic attack scenarios—based on known vulnerabilities, threat actor tactics, and business context—organizations can forecast the likelihood and impact of specific cyber events. This method supports both initial, high-level analysis and more detailed assessments, helping decision-makers prioritize resources and justify investments in security controls.
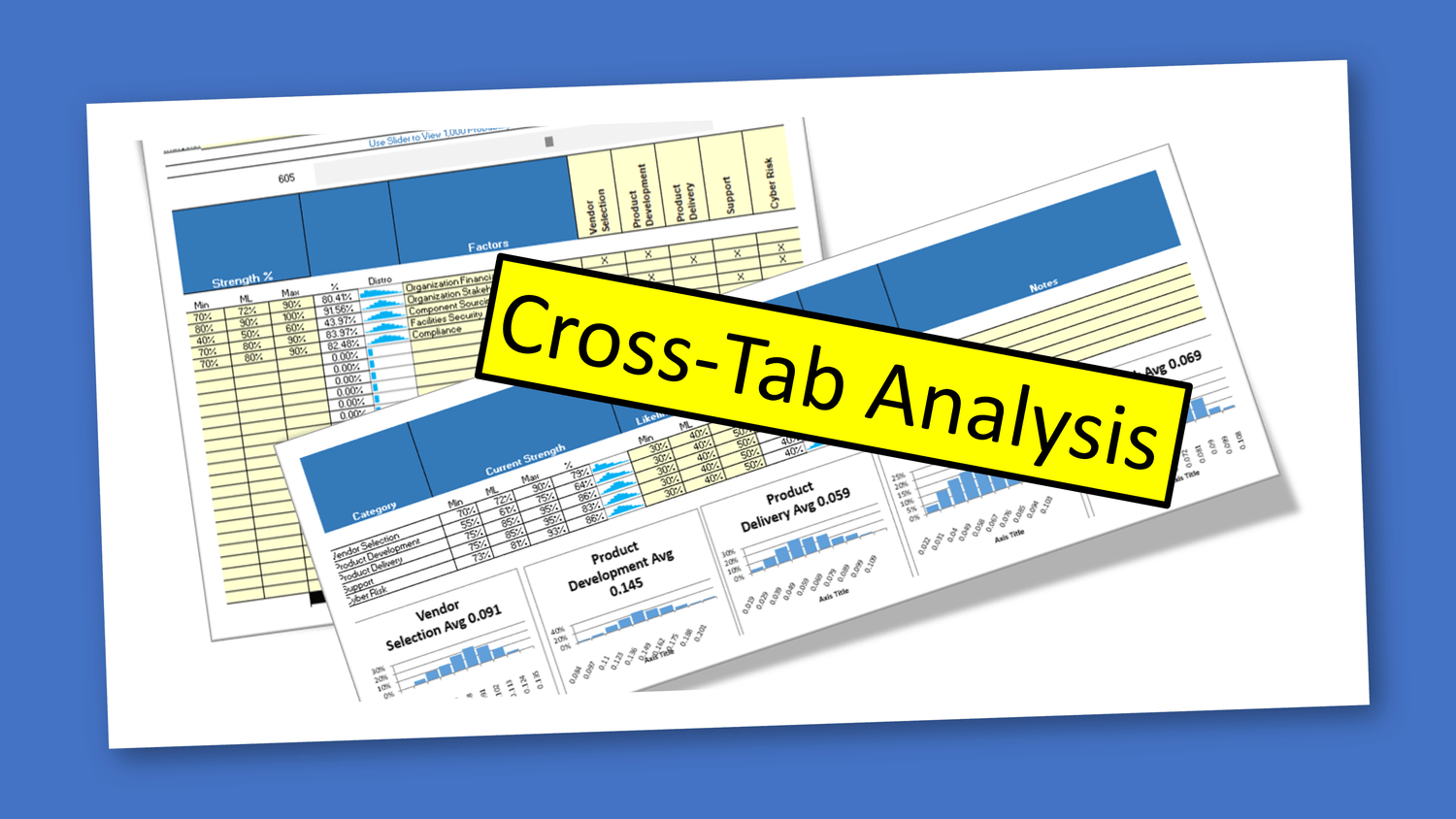
Probabilistic Methods and Monte Carlo Simulations For organizations seeking deeper insights, probabilistic methods such as Monte Carlo simulations offer powerful capabilities. These models use ranges of input values (minimum, most likely, maximum) to generate thousands of possible outcomes, producing probability distribution charts that visualize the likelihood of different risk scenarios. Monte Carlo simulations are ideal for forecasting the probability and financial impact of cyber attacks, supporting data-driven decisions and robust risk management strategies.
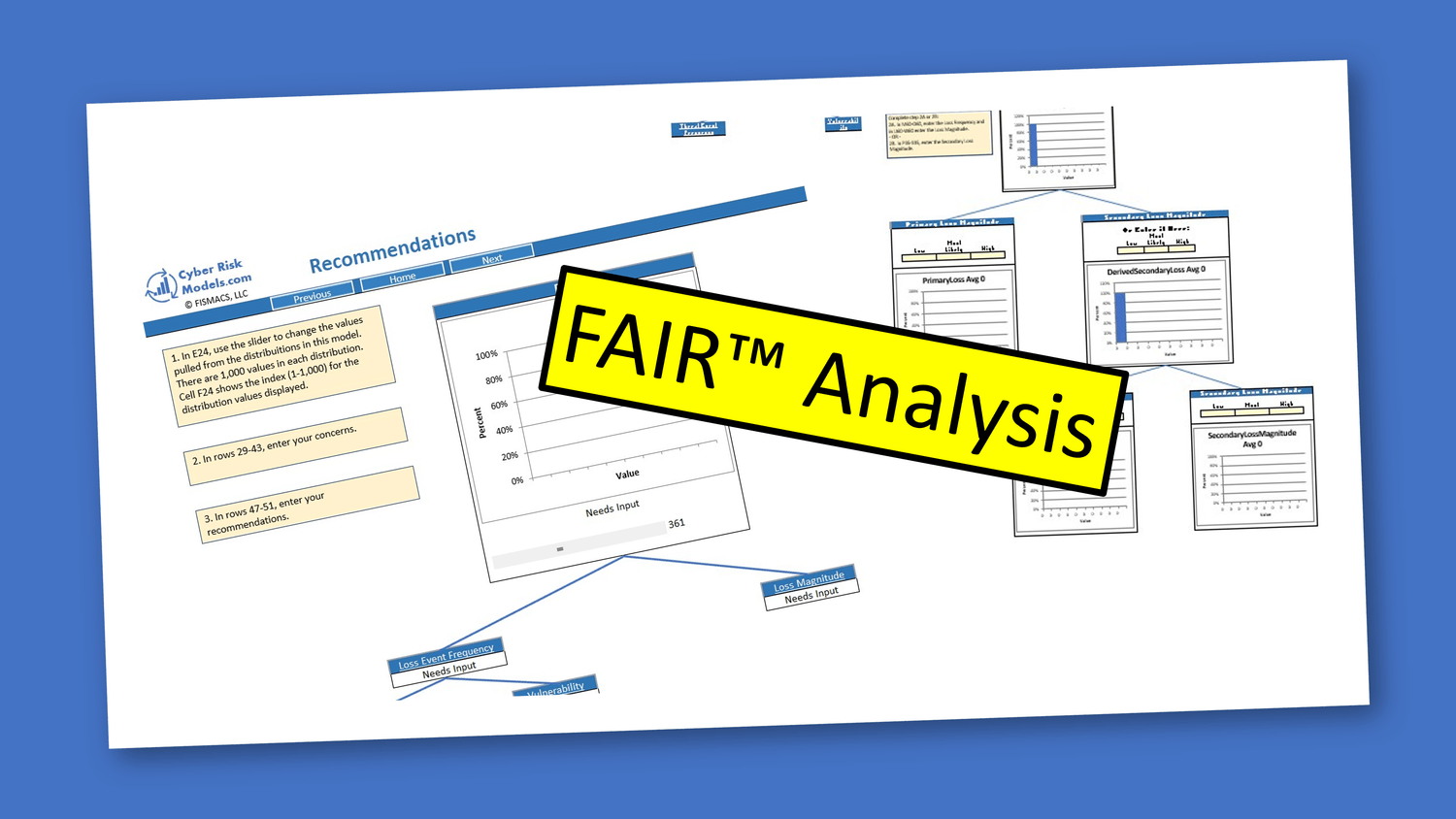
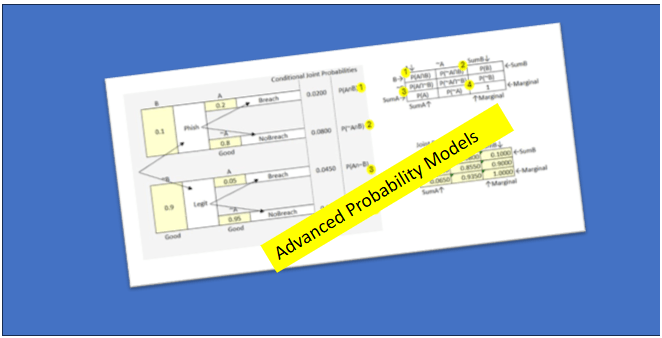
Bayesian Modeling: The Learning Algorithm Advanced custom models can incorporate Bayesian inference, the same “learning” algorithm at the core of all machine learning and AI systems. In cyber risk modeling, Bayesian methods allow organizations to refine risk estimates as new information becomes available. By updating prior assumptions with observed evidence, Bayesian models adapt to changing conditions and evolving threats, making them especially valuable for environments where risk factors shift over time. This approach supports continuous improvement in risk forecasting and decision-making as your organization gathers more data and experience.
Risk Model Use Cases
Attack Scenario: To understand the likelihood that a particular vulnerability will be leveraged against you in a cyberattack, this is a good choice. This is also a good choice if you want to go beyond tabletop exercises and increase the likelihood of a scenario resulting in a negative outcome.
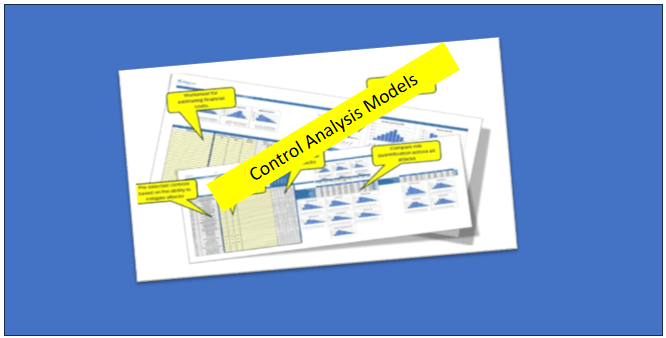
Measuring Control Strength: This type of model will use one of two advanced probabilistic methods to forecast the outcome when pitting a threat actor's strength against the estimated strength of your security controls. This is not unlike gaming theory where two strengths are compared over thousands of iterations to determine the most common or likely outcome.
Third Party Risk: This is a good example of a model that moves you from qualitative to quantitative by reviewing a series of questions (qualitative) and rating or scoring each, then aggregating the results and quantifying the results. This is also a good model to pair with the Attack Scenario model to then ask the question of risk from attack based on the 3rd party's risk score.
Insider Threat Modeling: It's not difficult to model the likelihood that any employee could be moved to becoming an insider threat capable of theft or damage. This type of model identifies not only the threshold where an employee is likely to transition into an insider threat but also how rapidly such activity would likely occur.
Forecasting Events: Several mathematical algorithms can be used to forecast the number and speed of events. Some estimate events as regular occurrences, while others forecast events increasing at a steady rate. Still others can take into consideration factors such as group behavior and random increases in frequency. Based on what you need in a model, one or all of these may be employed.
Multiple Probabilities: Sometimes it is helpful to consider all possible probabilities rather than just focusing on the likelihood of a negative event. For example, we may ask the likelihood that an email is malicious and that it leads to immediate compromise, but what about the probability that it is malicious and doesn't lead to immediate compromise? This is one method of verifying the effectiveness of controls on blocking the immediate compromise.
Financial and Operational Impacts: Along with estimating the likelihood of an attack or negative outcome, the same methods can be applied for estimating financial or operational impact. The risk of attack is a range of probabilities, and the same is true of impact. For this reason, it's often useful to include the ability to estimate these ranges as they are a great aid for planning purposes.
Pricing
Sample Models
Risk Model Development
$ 125/h
For CISOs who want to transition from qualitative to quantitative analysis.
Requirements documentation
Selection of methods and algorithms
Design and layout approval
Initial model approval
Final model delivery
Model documentation
Training
Get The Business Case
A simple justification for subscription you can share with management.
Name
We will not send spam

Risk Quantified
Don't miss the blind spots that others in your industry are getting hit with.

Financial Impacts
Express risk in financial terms so executives have an idea of the financial exposure.

Cost-Effective
Even the highest level of support is cost-effective compared to hiring even a single staff person.